Get the latest information about Set Up Secure Network Connection At A Remote Site in this article, hopefully providing better understanding for you.

Establishing a Secure Network Connection at Remote Sites: A Comprehensive Guide
As technology continues to advance, remote work and distributed teams have become increasingly common. However, establishing a secure network connection at remote sites poses unique challenges. In this article, we will delve into the intricacies of setting up a secure network connection at remote sites, exploring various methods, best practices, and potential pitfalls.
Remote Site Network Security
Securely connecting remote sites to a central network is paramount for ensuring data protection, maintaining regulatory compliance, and mitigating cyber threats. Factors such as limited bandwidth, unreliable connectivity, and diverse network infrastructures can complicate the task.
Defining Remote Site Network Security
Remote site network security involves implementing measures to protect network assets, data transmission, and user access at remote locations. This includes implementing authentication protocols, encryption mechanisms, access control policies, and intrusion detection systems. Effective remote site network security ensures data confidentiality, integrity, and availability.
Methods for Establishing Secure Network Connection at Remote Sites
1. Site-to-Site Virtual Private Network (VPN)
A VPN creates a secure tunnel between two or more private networks, allowing remote sites to connect securely over the public internet. VPNs provide encryption, authentication, and traffic management, offering a comprehensive solution for remote site network security.
2. Dedicated Leased Line
A dedicated leased line provides a direct, private connection between remote sites and the central network. While more expensive than options like VPNs, leased lines offer higher bandwidth, reliability, and consistent performance.
3. Multi-Protocol Label Switching (MPLS)
MPLS is a technology that creates virtual circuits over a wide-area network (WAN). It offers reliable, secure connections for remote sites, with features like traffic prioritization and Quality of Service (QoS) control.
4. Software-Defined Wide-Area Networking (SD-WAN)
SD-WAN is a software-based approach to managing WAN connections. It provides flexibility, agility, and cost optimization for remote site network connections. SD-WAN can integrate various technologies like VPNs and MPLS.
5. Cloud-Based Security Solutions
Cloud-based security solutions, such as Secure Access Service Edge (SASE), offer centralized security management and threat detection for remote sites. They combine multiple security functions into a single platform, simplifying and enhancing security.
Tips and Expert Advice
1. Conduct a Security Assessment
Before implementing a secure network connection, conduct a thorough security assessment of remote sites. This involves identifying potential vulnerabilities, such as outdated operating systems, weak passwords, and insecure applications.
2. Implement Strong Authentication
Implement strong authentication methods, such as two-factor authentication or multi-factor authentication (MFA), to prevent unauthorized access to remote sites.
3. Use Encryption
Encrypt all data transmitted over the network, including user credentials, sensitive data, and network traffic. Encryption ensures data confidentiality and protects it from unauthorized access.
4. Implement Intrusion Detection and Prevention Systems (IDS/IPS)
Deploy IDS/IPS systems at remote sites to detect and prevent malicious traffic, such as malware, denial-of-service attacks, and network intrusions.
5. Monitor Network Traffic
Continuously monitor network traffic to identify suspicious activity, potential threats, and any deviations from normal patterns.
FAQ
Q: What is the most secure method for establishing a remote site network connection?
A: The most secure method depends on the specific needs and constraints. Dedicated leased lines provide the highest level of security but are also the most expensive. VPNs and MPLS offer a balance of security and affordability.
Q: What are the potential risks of not implementing a secure network connection at remote sites?
A: Failure to establish a secure network connection can lead to data breaches, unauthorized access, malware infections, and network disruptions. These incidents can damage reputation, result in financial losses, and impact compliance with regulations.
Conclusion
Establishing a secure network connection at remote sites is crucial for maintaining data integrity, ensuring regulatory compliance, and preventing cyber threats. By understanding the different methods and best practices, organizations can effectively protect their network assets and data at remote locations. If you want to enhance the security of your remote site network connections, I encourage you to delve deeper into the resources provided in this article and consult with experienced security professionals.
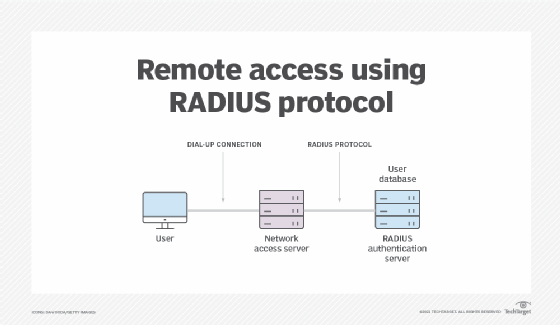
Image: www.techtarget.com
You have read Set Up Secure Network Connection At A Remote Site on our site. Thank you for your visit, and we hope this article is beneficial for you.